See the Internet in God Mode
Predict Cyber Attacks Earlier, Faster and More Accurately
Our Solutions for Predictive Threat Intelligence
45 billion data points
Interconnected data types including live routing, registration & resolution data.
18 source types
IPs, domains, ASNs, blacklists, whitelists, content links, and much more.
Real-time recency
Sub-millisecond response and real-time information updates.
See hidden connections
Unlimited data depth, unified data and infinite data traversal.
Reduce false positives
Multi-parameter in-depth scoring to improve accuracy.
Know threat contexts
Don’t just see the threat, understand why it matters.
Instant Insight. Automated Defense
Deeper Threat Context with Whisper Graph
Unlock the full potential of your cybersecurity solutions by enriching them with more data than ever before.
Real-time recency
6x more source types
20x more data points
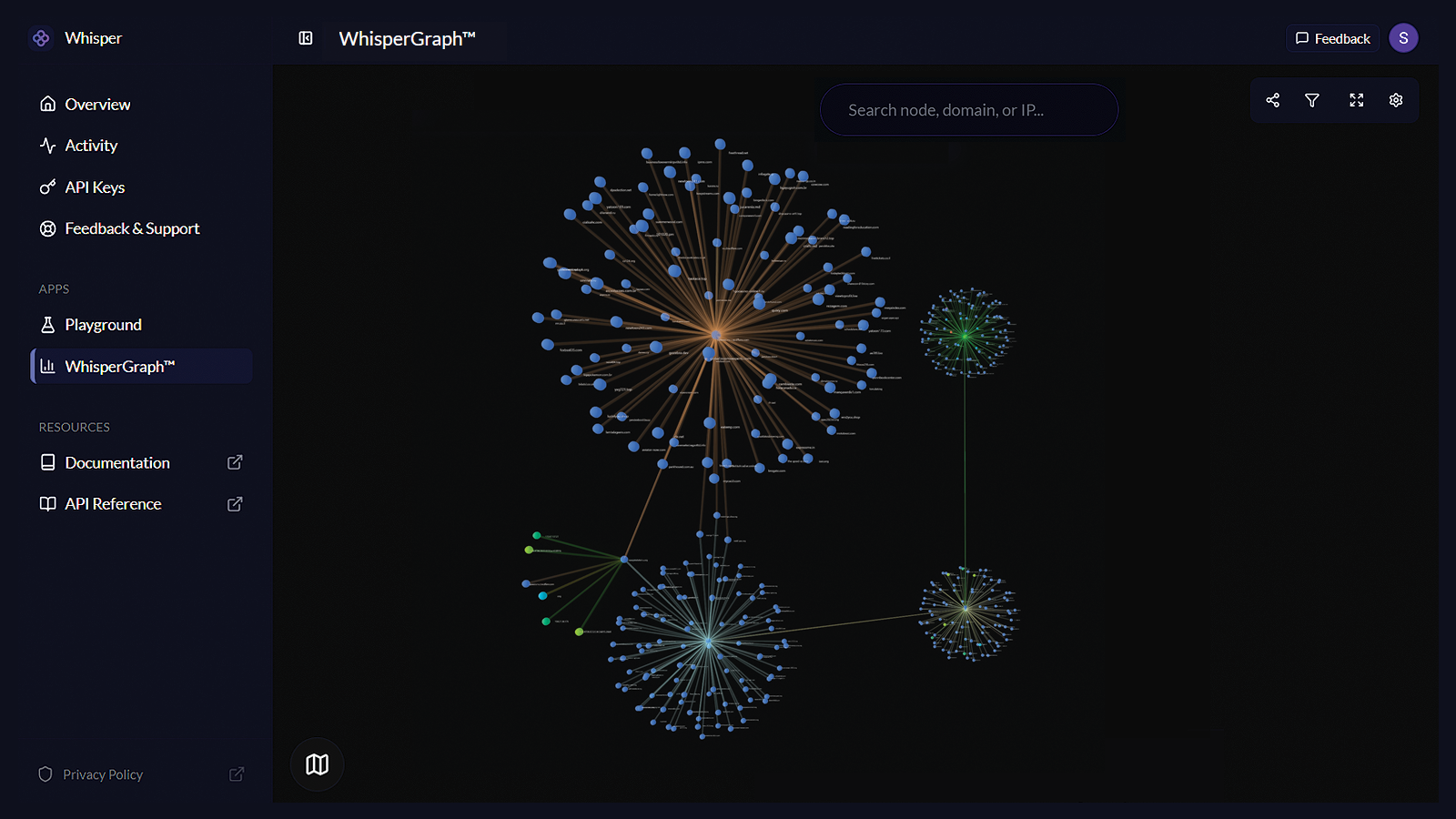

Unlock Cyber Visibility with Whisper Dashboard
Whisper transcends traditional threat intelligence, skyrocketing prediction and analytical capabilities.
Understand threat contexts
Cut false positives
Predict attacks earlier
Trusted by Cybersecurity Leaders
Here's what industry experts have to say about our technology.
CISO
Global NextGen IT Solutions Firm
Cybersecurity Analyst
Renowned Cybersecurity R&D Firm
Engineering Security Lead
Global Fintech Leader
Security Director
Leading Internet Authority
Stay Ahead of the Breach
Real-Time Insights. Pre-Attack Intelligence.
